https://techwirepro.com/
Experts debate online strings’ risks. Many users encounter odd codes daily. These codes spark curiosity and fear. People search for answers quickly. Understanding context prevents panic. Research reveals truths behind codes. Digital world hides potential dangers. Awareness protects personal data. Knowledge empowers safe navigation.
48ft3ajx appears in various contexts. It functions as a random identifier. Developers use it for tracking. URLs often contain such strings. Analytics tools employ them frequently. Session IDs resemble this format. Software generates them automatically. No inherent meaning exists alone.
Questions arise about safety. Users wonder is 48ft3ajx harmful. Investigations show no physical threat. It lacks chemical properties entirely. Biological risks remain absent. Environmental impact equals zero. Myths spread through misinformation. Facts debunk harmful claims.
What Exactly Is 48ft3ajx?
Programmers create alphanumeric strings. These serve multiple purposes online. 48ft3ajx fits this category perfectly. It identifies users temporarily. Marketing campaigns utilize similar codes. Databases store them for reference. Apps rely on them heavily. Security measures incorporate variations.
Random generation ensures uniqueness. Algorithms produce endless combinations. Length varies by application. 48ft3ajx has eight characters. Mix includes numbers and letters. Case sensitivity matters sometimes. Usage spans industries widely. Tech firms adopt them standardly.
No database lists it as hazardous. Regulatory bodies ignore such strings. EPA overlooks digital identifiers. OSHA focuses on physical safety. WHO deals with health issues. No records mention 48ft3ajx specifically. Experts confirm its neutrality. Context determines any risk.
The Digital Risks Associated
Cyber attackers exploit random strings. They hide malicious intent cleverly. Phishing links include odd codes. Malware uses them for obfuscation. Spam campaigns employ similar tactics. Browser hijacks involve such identifiers. Data breaches expose personal info. Privacy violations occur frequently.
Users click suspicious URLs unknowingly. Codes like 48ft3ajx mask destinations. Redirects lead to scam sites. Downloads install harmful software. Tracking profiles online behavior. Advertisers collect data aggressively. Hackers steal credentials easily. Financial losses mount quickly.
Social engineering tricks people. Fake messages contain these strings. Notifications lure clicks effectively. Apps request permissions unduly. Devices compromise security layers. Networks face intrusion attempts. Systems slow down noticeably. Recovery demands time and effort.

Debunking Myths About Harm
Rumors claim physical dangers. Some say it’s a chemical code. Others link to cosmetics ingredients. No evidence supports these. Scientific data lacks entirely. Databases show no matches. Experts dismiss such notions. Misunderstandings fuel false narratives.
Online forums spread confusion. Posts question is 48ft3ajx harmful. Answers vary wildly. Reliable sources clarify facts. No toxicity exists here. Ingestion impossible for strings. Contact poses no issue. Exposure means nothing physically.
Environmental claims fall flat. No pollution links appear. Biological agents differ greatly. Health agencies confirm safety. Public records remain clean. Investigations reveal digital nature. Myths persist despite evidence. Education counters misinformation effectively.
How Cybercriminals Use Such Codes
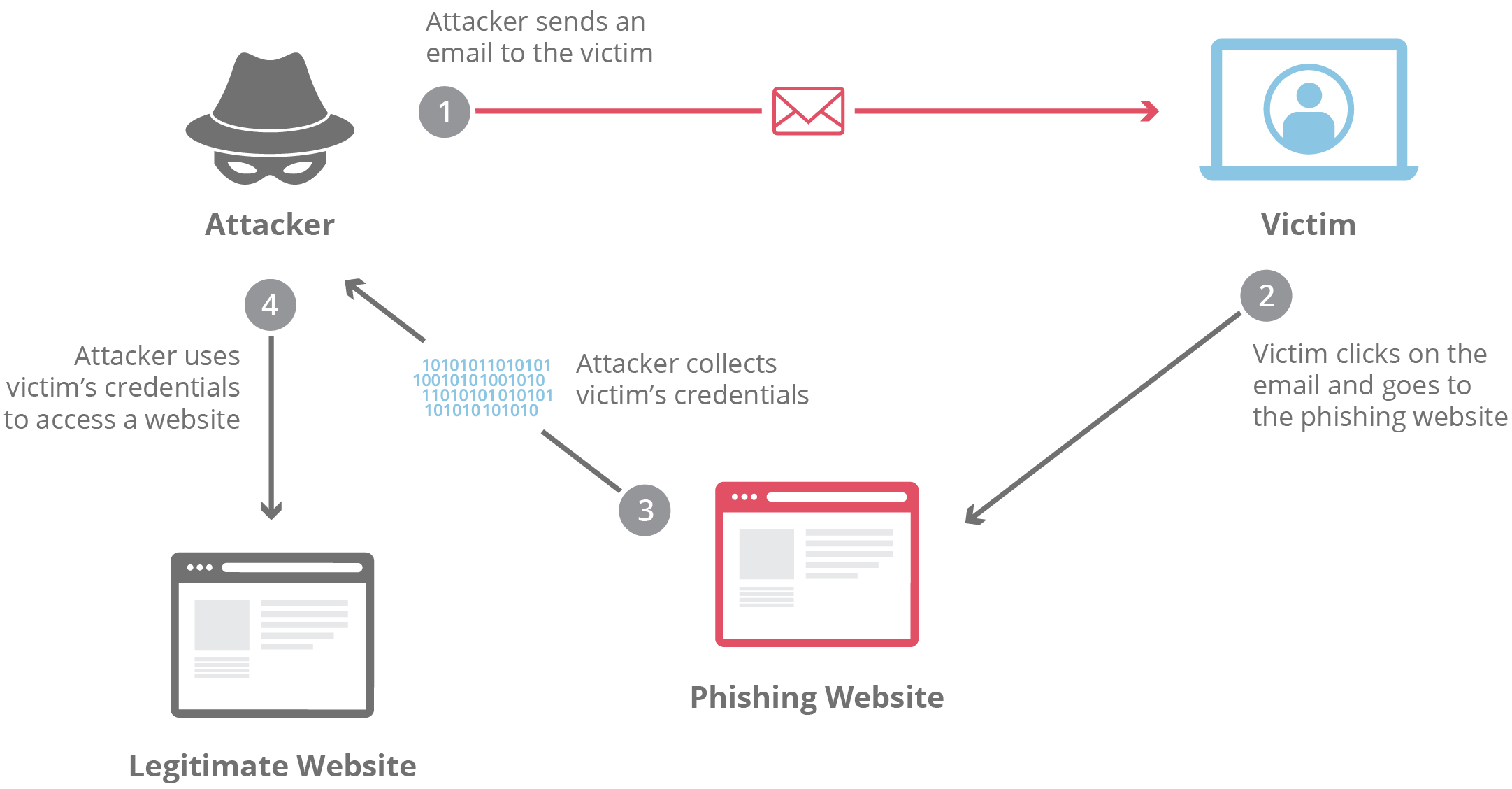
Attackers craft phishing emails. They embed codes in links. Victims click without caution. Sites mimic legitimate ones. Credentials enter fake forms. Data transmits to hackers. Accounts compromise instantly. Identity theft follows soon.
Malware hides in downloads. Codes name infected files. Users open attachments blindly. Viruses spread through networks. Ransomware locks data firmly. Payments demand high sums. Backups save situations often. Prevention beats cure always.
Shortened URLs conceal dangers. Services generate random strings. 48ft3ajx could appear there. Redirects surprise users. Malicious pages load quickly. Scripts run automatically. Devices infect silently. Awareness reduces risks significantly.
Prevention Strategies for Users
Install antivirus software promptly. Update it regularly. Scan systems weekly. Block suspicious links automatically. Firewalls enhance protection layers. Browsers offer safe modes. Extensions reveal URL destinations. Hover before clicking always.
Educate yourself on threats. Read cybersecurity articles often. Recognize phishing signs clearly. Verify sender identities. Avoid unsolicited messages. Report spam immediately. Change passwords frequently. Use managers for complexity.
Enable two-factor authentication. Apps provide extra security. Codes send via text. Biometrics add layers. Monitor accounts daily. Check for unusual activity. Freeze credit if needed. Stay vigilant constantly.
Case Studies of Similar Incidents
Major breach involved random codes. Hackers used strings in URLs. Thousands affected worldwide. Data leaked massively. Companies paid fines heavily. Users sued for damages. Lessons learned improved protocols. Security tightened afterward.
Phishing campaign targeted banks. Codes hid malicious sites. Customers lost savings. Investigations traced origins. Criminals arrested eventually. Media covered stories widely. Awareness rose sharply. Prevention measures adopted quickly.
Software vulnerability exploited codes. Apps generated insecure IDs. Attackers guessed patterns easily. Systems compromised broadly. Patches released urgently. Users updated devices. Incidents decreased notably. Research continued ongoing.
Expert Opinions on the Matter
Cybersecurity pros analyze strings. They see no direct harm. Context matters most. Randomness evades detection. Tools identify patterns now. AI enhances threat hunting. Predictions forecast more sophistication. Vigilance remains key.
Analysts debunk physical risks. No agency regulates digital codes. Focus shifts to usage. Malicious intent defines danger. Education trains users effectively. Workshops teach recognition skills. Certifications boost knowledge. Communities share experiences.
Researchers study obfuscation techniques. Codes like 48ft3ajx feature prominently. Papers detail evasion methods. Conferences discuss findings. Solutions emerge collaboratively. Innovations protect better. Future looks secure gradually. Progress depends on adoption.

Addressing Common Questions
People ask is 48ft3ajx harmful often. Answers depend on context. Digital use poses risks. Physical harm absent completely. Verification checks legitimacy. Tools analyze strings. Reports guide actions. Caution advises restraint.
Searches reveal mixed results. Sites discuss potential dangers. Reliable sources clarify. Myths confuse seekers. Facts ground discussions. Experts provide insights. Communities debate openly. Resolutions form consensus.
Queries spike during incidents. Media amplifies concerns. Investigations calm fears. Data supports conclusions. Trends show patterns. Predictions aid preparation. Strategies evolve constantly. Adaptation ensures safety.
The Role of Technology in Safety
AI detects malicious codes. Algorithms scan URLs swiftly. Machine learning improves accuracy. Databases store threat intel. Sharing enhances protection. Cloud services offer shields. Devices integrate defenses. Updates fix vulnerabilities.
Browsers warn about risks. Pop-ups alert users. Settings customize security. Extensions add features. Developers code safely. Standards guide practices. Audits check compliance. Certifications assure quality.
Networks monitor traffic. Firewalls block intrusions. Encryption secures data. Backups restore losses. Training programs educate staff. Policies enforce rules. Audits reveal weaknesses. Improvements follow findings.
Future Outlook on Digital Identifiers
Innovation creates new codes. Quantum computing challenges security. Blockchain offers alternatives. Standards evolve rapidly. Regulations catch up slowly. International cooperation grows. Threats adapt cleverly. Defenses strengthen accordingly.
Users demand transparency. Companies provide details. Privacy laws enforce rights. Fines deter violations. Awareness campaigns inform public. Schools teach basics. Media reports responsibly. Society benefits overall.
Predictions foresee safer web. Tools advance detection. AI leads the way. Collaboration defeats threats. Vigilance sustains progress. Education empowers individuals. Technology enables protection. Future holds promise.
Conclusion: Weighing the Evidence
Reviews show no inherent harm. Context defines any danger. Users stay informed wisely. Precautions minimize risks. Experts agree on facts. Myths fade with knowledge. Safety prevails through action.
Final thoughts address is 48ft3ajx harmful. No direct threat exists. Digital caution advised. Physical worries unfounded. Research supports this view. Awareness guides behavior. Protection ensures peace.
Frequently Asked Questions(FAQs)
Is 48ft3ajx a virus or malware?
Not inherently. 48ft3ajx is simply an alphanumeric identifier. Context determines safety—verify the source and scan with updated antivirus software if concerned.
Can 48ft3ajx steal my personal information?
The code itself cannot. However, if it’s part of a phishing attempt or malicious software, the associated system could pose risks. Always verify legitimacy before interacting.
Should I delete files or products labeled 48ft3ajx?
Not automatically. First identify what it represents through proper verification methods. Deletion without understanding could cause system issues or waste legitimate products.
How do I know if 48ft3ajx is legitimate?
Verify through official channels contact the manufacturer, check against legitimate databases, examine source credibility, and look for proper documentation and safety information.
What industries commonly use codes like 48ft3ajx?
Software development, manufacturing, logistics, pharmaceuticals, chemicals, cybersecurity, and database management frequently use similar alphanumeric identifiers for tracking and reference purposes.
Can 48ft3ajx cause physical harm?
If it identifies a chemical or physical product, potential harm depends on the substance itself. Always consult Safety Data Sheets and manufacturer documentation before handling unknown materials.
Where should I report suspicious use of codes like 48ft3ajx?
Report to relevant authorities based on context: FTC for consumer fraud, FBI IC3 for cybercrime, FDA for food/drug issues, or EPA for environmental concerns.
Read more knowledgeable blogs on: techwirepro.com